Practical exercizes
To be completed by 3/23/2005
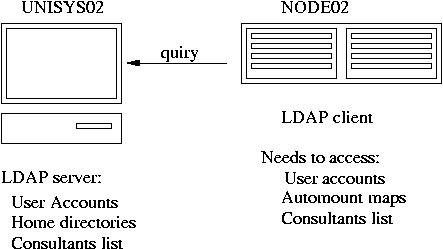
Objective:
Setup OpenLDAP server on your desktop and OpenLDAP client on the node.
1. Install OpenLDAP packages
On the server:
slapd
ldap-utils
libldap2
On the client:
ldap-utils
libldap2
libnss-ldap
libpam-ldap
You can exit the configuration stage since you will configure LDAP
manually. Remove the databases created during LDAP setup:
rm -rf /var/lib/ldap/*
2. Setup LDAP server.
Create file /etc/ldap/slapd.conf
Choose a unique dc (Domain Component) name, for example,
dc=uni02, dc=unisys, dc=com if you are using
unisys02 and node02.
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
# Include Schemas
include /etc/ldap/schema/core.schema
include /etc/ldap/schema/cosine.schema
include /etc/ldap/schema/nis.schema
include /etc/ldap/schema/inetorgperson.schema
# Where the dynamically loaded modules are stored
modulepath /usr/lib/ldap
moduleload back_ldbm
# ldbm database definitions
database ldbm
# Define Domain components and Root distinguished name (Manager)
suffix "dc=uni02, dc=unisys, dc=com"
rootdn "cn=Manager,dc=uni02,dc=unisys,dc=com"
# Where the database file are physically stored for database #1
directory "/var/lib/ldap"
# Cleartext passwords, especially for the rootdn, should
# be avoided. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
# Root password can be created with:
# perl -e "print crypt(thisp, ac,)" > pass.txt
# rootpw thisp
rootpw {crypt}acunRNwFPEdHQ
# slapd process ID file
pidfile /var/run/slapd/slapd.pid
|
3. start LDAP:
/etc/init.d/slapd start
To make sure LDAP is running, execute ldapsearch:
ldapsearch -x -LL -b '' -s base '(objectclass=*)' namingContexts
You should see:
namingContexts: dc=uni02,dc=unisys,dc=com
4. Bind the client, node02, to the server by editing file /etc/ldap/ldap.conf
and leaving uncommented only two entries:
HOST unisys02
BASE dc=uni02,dc=unisys,dc=com
Similarly, bind the server, unisys02, to itself by creating the same file,
/etc/ldap/ldap.conf
5. Outline of the directory is the following:
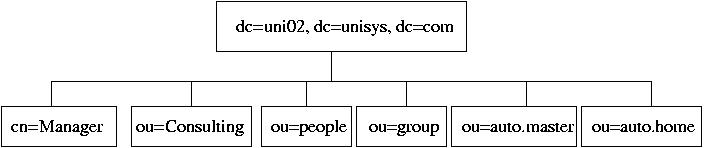
On the server, create LDIF file, init.ldif, so far,
including only a part of the Directory:
dn: dc=uni02,dc=unisys,dc=com
dn: cn=Manager, dc=uni02, dc=unisys, dc=com
dn: ou=Consulting, dc=uni02,dc=unisys,dc=com
and a few cn entries for ou=Consulting:
dn: cn=Dennis Ritchie, ou=Consulting, dc=uni02,dc=unisys,dc=com
dn: cn=Ken Thompson , ou=Consulting, dc=uni02,dc=unisys,dc=com
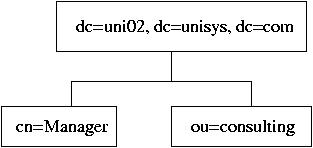
# Root node
dn: dc=uni02,dc=unisys,dc=com
objectclass: organization
objectclass: dcObject
o: uni02.unisys.com
dc: uni02
# The list branch node
dn: ou=Consulting, dc=uni02,dc=unisys,dc=com
objectclass: organizationalUnit
ou: Consulting
# The Super-User's node
dn: cn=Manager, dc=uni02, dc=unisys, dc=com
objectclass: organizationalRole
cn: Manager
# A leaf node
dn: cn=Dennis Ritchie, ou=Consulting, dc=uni02,dc=unisys,dc=com
objectclass: person
cn: Dennis Ritchie
sn: Ritchie
# Another leaf node
dn: cn=Ken Thompson , ou=Consulting, dc=uni02,dc=unisys,dc=com
objectclass: person
cn: Ken Thompson
sn: Thompson
|
6. ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f init.ldif
7. On the client, node02, run
ldapsearch -x -L -b 'dc=uni02,dc=unisys,dc=com' '(objectclass=*)'
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' '(cn=*)'
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' '(cn=Ken Thompson)'
8. Create a new LDIF file, people.ldif:
dn: ou=passwords, dc=uni02, dc=unisys, dc=com
ou: passwords
objectclass: organizationalUnit
dn: ou=group, dc=uni02, dc=unisys, dc=com
ou: group
objectclass: organizationalUnit
|
9. Add it to the LDAP database:
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f people.ldif
Check if the "ou" entries are in the database. On the client, run
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com'
10. Delete Organizational Units "passwords" and "group":
create a file, delp.txt:
ou=passwords, dc=uni02, dc=unisys, dc=com
ou=group, dc=uni02, dc=unisys, dc=com
Run
ldapdelete -x -D "cn=manager,dc=uni02,dc=unisys,dc=com" -W -f delp.txt
11. Modify people.ldif:
dn: ou=People, dc=uni02, dc=unisys, dc=com
ou: People
objectclass: organizationalUnit
dn: ou=group, dc=uni02, dc=unisys, dc=com
ou: group
objectclass: organizationalUnit
|
Run
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f people.ldif
12. On the server, enable shadow passwords by running command
pwconv
Create a new user group, ldap:
groupadd -g 1200 ldap
Create a new user, say, jack:
useradd -u 1200 -g 1200 -m -s /bin/bash jack
Set a password for the user.
Install migradiontools package on the server:
apt-get install migrationtools
Copy common, password, and group migration Perl scripts from
/usr/share/migrationtools into your current directory.
cp /usr/share/migrationtools/migrate_passwd.pl .
cp /usr/share/migrationtools/migrate_group.pl .
cp /usr/share/migrationtools/migrate_common.ph .
Modify file migrate_common.ph:
# Default DNS domain
$DEFAULT_MAIL_DOMAIN = "unisys02.unisys.com";
# Default base
$DEFAULT_BASE = "dc=uni02,dc=unisys,dc=com";
# turn this on to support more general object clases
# such as person.
$EXTENDED_SCHEMA = 1;
$USE_UTF8 = 0;
# Uncomment these to exclude Debian-managed system users and groups
$IGNORE_UID_BELOW = 1200;
$IGNORE_GID_BELOW = 1200;
# And here's the opposite for completeness
$IGNORE_UID_ABOVE = 9999;
$IGNORE_GID_ABOVE = 9999;
Comment out the DEFAULT_REALM setting in the EXTENDED schema settings.
# $DEFAULT_REALM = $DEFAULT_MAIL_DOMAIN;
# $DEFAULT_REALM =~ tr/a-z/A-Z/;
By using the migration script, migrate user accounts into LDIF file passwd.ldif: