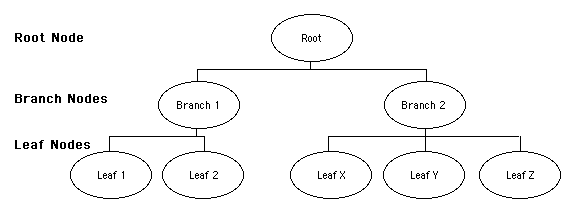
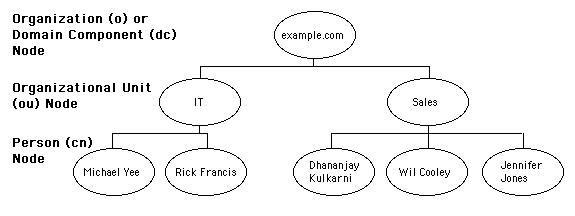
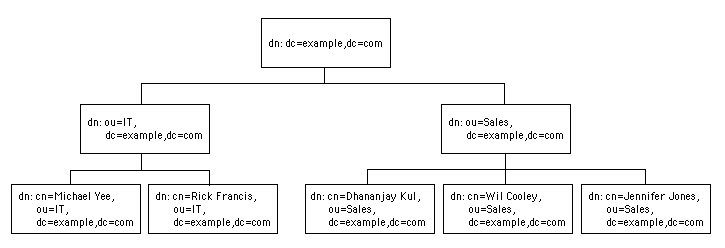
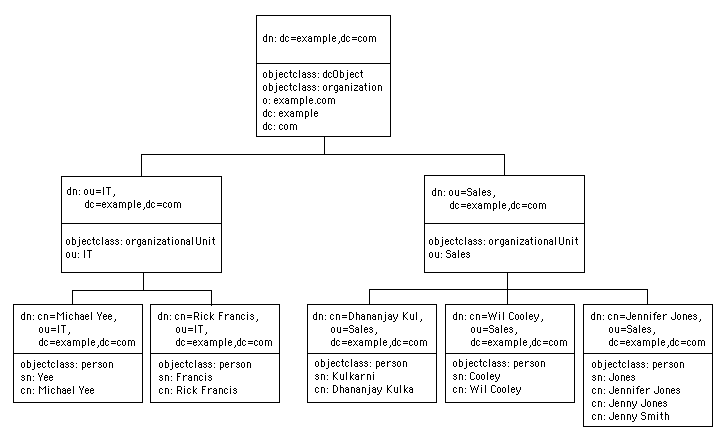
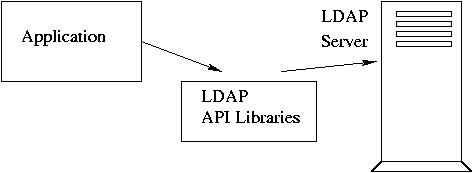
LDAP API are available for a number of programming languages, including
C, Java, and Perl.
Application example:
Apache web server
E-mail clients: Netscape, Mozilla, Outlook
Sendmail
Samba
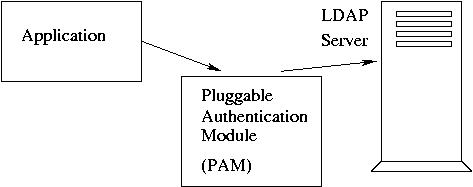
LDAP for user Authentication:
Services example
login, rlogin, rsh, rexec, ftp, passwd, su, sudo, ssh, imap, pop3, xdm...
To work with LDAP, PAM modules should be configured for accessing LDAP.
/etc/nsswitch.conf also should be configured to point at LDAP.
Graphical LDAP tools
Kldap
KDirAdm
Directory Administrator.
GQ
LDAP Browser/Editor
References:
Excellent LDAP tutorial (by Michael Yee): most of the lecture material is based on it.
Very good LDAP lectures and tutorials (by Brad Marshall)
OpenLDAP Administrator's Guide
pGina for a Windows LDAP client.
-------------------------------------------------
Assignment due by 03/17/2004
Objective:
1. Install OpenLDAP packages if they haven't been installed yet (RPM files
from the distribution directory at 192.168.5.250:/usr/src/cd90/).
On the server:
openldap
openldap-servers
openldap-clients
nss_ldap
On the client:
openldap
openldap-clients
nss_ldap
2. Setup LDAP server.
Create file /etc/openldap/slapd.conf
Choose a unique dc (Domain Component) name, for example,
dc=uni02, dc=unisys, dc=com:
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
#######################################################################
# ldbm database definitions
#######################################################################
database ldbm
suffix "dc=uni02, dc=unisys, dc=com"
rootdn "cn=Manager,dc=uni02, dc=unisys, dc=com"
# Cleartext passwords, especially for the rootdn, should
# be avoided. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
# Root password can be created with:
# perl -e "print crypt(thisp, ac,)" > pass.txt
#rootpw thisp
rootpw {crypt}acunRNwFPEdHQ
|
3. start LDAP:
/etc/rc.d/init.d/ldap start
To make sure LDAP is running, execute ldapsearch:
ldapsearch -x -LL -b '' -s base '(objectclass=*)' namingContexts
You should see:
namingContexts: dc=uni02,dc=unisys,dc=com
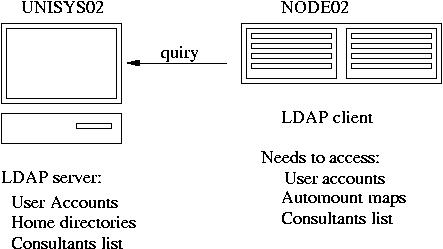
4. On the client, modify file /etc/openldap/ldap.conf:
HOST unisys02
BASE dc=uni02,dc=unisys,dc=com
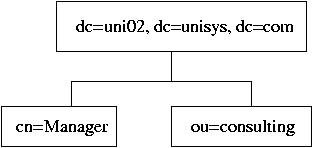
5. Outline of the directory is the following:
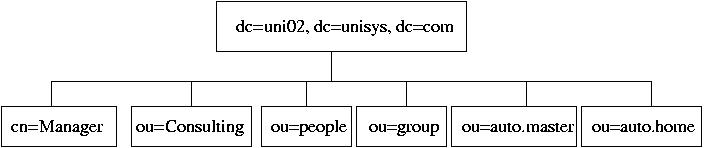
On the server, create LDIF file, init.ldif, so far,
including only a part of the Directory:
dn: dc=uni02,dc=unisys,dc=com
dn: cn=Manager, dc=uni02, dc=unisys, dc=com
dn: ou=Consulting, dc=uni02,dc=unisys,dc=com
and a few cn entries for ou=Consulting:
dn: cn=Dennis Ritchie, ou=Consulting, dc=uni02,dc=unisys,dc=com
dn: cn=Ken Thompson , ou=Consulting, dc=uni02,dc=unisys,dc=com
# Root node
dn: dc=uni02,dc=unisys,dc=com
objectclass: organization
objectclass: dcObject
o: uni02.unisys.com
dc: uni02.unisys.com
# The list branch node
dn: ou=Consulting, dc=uni02,dc=unisys,dc=com
objectclass: organizationalUnit
ou: Consulting
# The Super-User's node
dn: cn=Manager, dc=uni02, dc=unisys, dc=com
objectclass: organizationalRole
cn: Manager
# A leaf node
dn: cn=Dennis Ritchie, ou=Consulting, dc=uni02,dc=unisys,dc=com
objectclass: person
cn: Dennis Ritchie
sn: Ritchie
# Another leaf node
dn: cn=Ken Thompson , ou=Consulting, dc=uni02,dc=unisys,dc=com
objectclass: person
cn: Ken Thompson
sn: Thompson
|
6. ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f init.ldif
7. On the client, node02, run
ldapsearch -x -L -b 'dc=uni02,dc=unisys,dc=com' -W '(objectclass=*)'
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' '(cn=*)'
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' '(cn=Ken Thompson)'
8. Create a new LDIF file, people.ldif:
dn: ou=passwords, dc=uni02, dc=unisys, dc=com
ou: passwords
objectclass: organizationalUnit
dn: ou=group, dc=uni02, dc=unisys, dc=com
ou: group
objectclass: organizationalUnit
|
9. Add it to the LDAP database:
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f people.ldif
Check if the "ou" entries are in the database. On the client, run
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com'
10. Delete Organizational Units "passwords" and "group":
create a file, delp.txt:
ou=passwords, dc=uni02, dc=unisys, dc=com
ou=group, dc=uni02, dc=unisys, dc=com
Run
ldapdelete -x -D "cn=manager,dc=uni02,dc=unisys,dc=com" -W -f delp.txt
11. Modify people.ldif:
dn: ou=People, dc=uni02, dc=unisys, dc=com
ou: People
objectclass: organizationalUnit
dn: ou=group, dc=uni02, dc=unisys, dc=com
ou: group
objectclass: organizationalUnit
|
Run
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f people.ldif
12. On the server, create a new user, say, jack. Set a password for the
user.
Copy password and group migration Perl scripts from
/usr/share/openldap/migration into your current directory.
cp /usr/share/openldap/migration/migrate_passwd.pl .
cp /usr/share/openldap/migration/migrate_group.pl .
cp /usr/share/openldap/migration/migrate_common.ph .
Modify migrate_passwd.pl and migrate_group.pl changing require ... for
require 'migrate_common.ph';
Modify migrate_common.ph,
# Default DNS domain
$DEFAULT_MAIL_DOMAIN = "unisys02.unisys.com";
# Default base
$DEFAULT_BASE = "dc=uni02,dc=unisys,dc=com";
# turn this on to support more general object clases
# such as person.
$EXTENDED_SCHEMA = 1;
Using the migration script, migrate user accounts into LDIF file passwd.ldif:
./migrate_passwd.pl /etc/passwd > passwd.ldif
Edit passwd.ldif removing everything except entries for user jack.
Modify slapd.conf including the following schemas:
include /etc/openldap/schema/redhat/rfc822-MailMember.schema
include /etc/openldap/schema/redhat/autofs.schema
include /etc/openldap/schema/redhat/kerberosobject.schema
Restart LDAP:
/etc/rc.d/init.d/ldap stop
/etc/rc.d/init.d/ldap start
Add the new user entry to the database:
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f passwd.ldif
13. Create a group LDIF file using migrate_group.pl script:
./migrate_group.pl /etc/group > group.ldif
Edit group.ldif removing all entries except for user jack.
Add the group entries to LDAP database:
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f group.ldif
On the client, node02, run ldapsearch on user jack to make sure the user
entries are in the database:
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' 'cn=jack'
14. Bind the client, node02, to the LDAP server:
mv /etc/ldap.conf /etc/ldap.conf-orig
ln -s /etc/openldap/ldap.conf /etc/ldap.conf
Modify /etc/nsswitch.conf:
passwd: files ldap
shadow: files ldap
group: files ldap
automount: ldap
Backup the following PAM modules in /etc/pam.d:
passwd, login, rsh, rlogin, rexec, sshd, su.
Copy PAM modules with the same name from /usr/share/doc/nss_ldap-202/pam.d/
into /etc/pam.d. Note, ssh is copied to sshd. Restart sshd.
Check if the client recognizes user jack:
id jack
If so, rsh to the client from the server as user jack:
rsh -l jack node02
15. Secure access to LDAP directory adding the following access rules to
the end of slapd.conf:
#Access control
access to attr=userPassword
by self write
by anonymous auth
by dn="cn=Manager,dc=uni02,dc=unisys,dc=com" write
by * compare
access to *
by self write
by dn="cn=Manager,dc=uni02,dc=unisys,dc=com" write
by * read
|
Make sure the passwords doesn't show up on the client when you run
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' 'cn=jack'
16. Login to the client, node02, as user jack. Change password running
command passwd.
Has the password been changed in LDAP databases?
Has it been changed in /etc/shadow on the server?
On the server, delete user jack:
/usr/sbin/userdel jack
Try to login to the client as user jack again.
17. Set the server to authenticate LDAP users, repeating Ex. #14.
Login to the server as user jack or su - jack. Do you get
into the home directory correctly?
As root, create a new directory /home/LDAP and migrate the LDAP user
home directory there:
mkdir /home/LDAP
cp -dpR jack LDAP
rm -rf jack
Modify /etc/exports to export directory /home/LDAP to the client;
run /usr/sbin/exportfs -a
Modify the entry for jack in the LDAP databases. You can accomplish
it deleting the entry and re-creating it again with the new
home directory, for example, run
ldapdelete -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f delu.txt
where file delu.txt contains the following entry:
uid=jack, ou=People, dc=uni02, dc=unisys, dc=com
Correct the home directory entry in passwd.ldif,
"homeDirectory: /home/LDAP/jack" and run
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f passwd.ldif
18. Create LDIF file, automount.ldif, for NFS automounts.
On node02, we need to mount unisys02:/home/LDAP onto /home/LDAP.
Contents of automount.ldif:
dn: ou=auto.master,dc=uni02,dc=unisys,dc=com
objectClass: top
objectClass: automountMap
ou: auto.master
dn: ou=auto.home,dc=uni02,dc=unisys,dc=com
objectClass: top
objectClass: automountMap
ou: auto.home
dn: cn=/home, ou=auto.master,dc=uni02,dc=unisys,dc=com
objectClass: automount
automountInformation: ldap:ou=auto.home,dc=uni02,dc=unisys,dc=com --timeout 60
cn: /home
dn: cn=LDAP,ou=auto.home,dc=uni02,dc=unisys,dc=com
objectClass: automount
automountInformation: -rw,hard,intr unisys02:/home/LDAP
cn: LDAP
|
Update the LDAP database:
ldapadd -x -D 'cn=Manager,dc=uni02,dc=unisys,dc=com' -W -f automount.ldif
Check if the client, node02, can access the maps through LDAP:
ldapsearch -x -LL -b 'dc=uni02,dc=unisys,dc=com' '*'
If you see the NFS maps, restart autofs on the client:
/etc/rc.d/init.d/autofs stop
/etc/rc.d/init.d/autofs start
SSH to node02 as user jack:
ssh jack@node02
You should get into his home directory mounter over NFS from the server.
19. Create an entry in /etc/hosts.deny on the LDAP server:
slapd: ALL
Check id you can run ldapsearch on the client.
Overwrite the denial to access slapd in /etc/hosts.allow:
slapd: 192.168.5.22 127.0.0.1
Run ldapsearch again on the client.
20. Download RPM for Directory Administrator.
Install using RPM on the LDAP server. Start Directory Administrator
and configure it:
/usr/bin/directory_administrator
During configuration, point it to the localhost, 127.0.0.1;
search root directory is dc=uni02, dc=unisys, dc=com; DN/User ID:
cn=Manager, dc=uni02, dc=unisys, dc=com; user Manager's password.
Create a new group, LDAP under ou=group, dc=uni02, dc=unisys, dc=com.
Create a new user in this group. Point its home directory to
/home/LDAP/[user_name]. Substitute the actual user name for [user_name].
Manually create a home directory for the user
mkdir /home/LDAP/[user_name]
cp /etc/skel/.* /home/LDAP/[user_name]
chown -R [user_name]:LDAP /home/LDAP/[user_name]
Try to ssh to the client as the new user.